ポケモンカード 長場雄 プロモカード
(税込) 送料込み
商品の説明
金欠のための新品です。
商品は写真のとおりとなります。
希少価値は高いと思いますのでご検討ください。
新品未開封商品となります。中身で評価する方は購入をお控えくださいませ。
〜以下検索用〜
ポケモンカード、大量、未開封、sr、プロモ、リザードン 、box、ボスの司令、リーリエ、旧裏面、ポケモンカードゲーム、gx、まとめ、未開封、引退、psa、ピカチュウ、ひかる、ミュウツー、高騰
仰天のボルテッカー、伝説の鼓動、ムゲンゾーン、爆炎ウォーカー、反逆クラッシュ、ソード&シールド、サン&ムーン、強化拡張パック、C、U、R、RR、RRR、TR、SR、UR、HR、PR、AR、ポケカ
クロバットv、ワタシラガv、ピカチュウ、デデンネgx 、ザシアンv、アルセウス&ディアルガ&パルキアGX、リザードンGX、レシラム&リザードンGX、ピカチュウ&ゼクロムGX
ポケモン HR hr SR sr SSR ssr RR rr
SA sa CHR chr 未開封品 シュリンク付き
ポケモンカード ポケカ
25th ANNIVERSARY Collection
フュージョンアーツ 蒼空ストリーム
摩天パーフェクト イーブイヒーローズ 漆黒のガイスト
白銀のランス 双璧のファイター 一撃マスター
連撃マスター シャイニースターV
仰天のボルテッカー タッグオールスターズ
ドリームリーグ オルタージェネシス ダブルブレイズ
タッグボルト ミラクルツイン ソード シールド ピカチュウ イーブイ ブラッキー ニンフィア
リザードン ミュウ 三神 ザシアン ピカゼク
ゲコゾロ レシリザ デデンネ クロバット
ムゲンダイナ ウーラオス マリィ メイ
アセロラ エリカ マオ&スイレンシロナ
リーリエ ブルーの探索 ゲンガー&ミミッキュGX シュリンク付き
スカーレット&バイオレット 強化拡張パック レイジングサーフ
ブランド:ポケモンカードゲーム
パッケージ:パック
1パックあたり枚数:5.0 枚
言語:日本語商品の情報
| カテゴリー | おもちゃ・ホビー・グッズ > トレーディングカード > ポケモンカードゲーム |
|---|---|
| 商品の状態 | 新品、未使用 |

イーブイたちが「YU NAGABA × ポケカ」コラボ第2弾に新登場

YU NAGABA×ポケモンカードゲーム」コラボレーションが実現

ピカチュウ YU NAGABA × ポケモンカード 長場雄 プロモカード 限定

ポケモンカード 長場雄 Nagaba コラボ プロモカード 全種 コンプリート
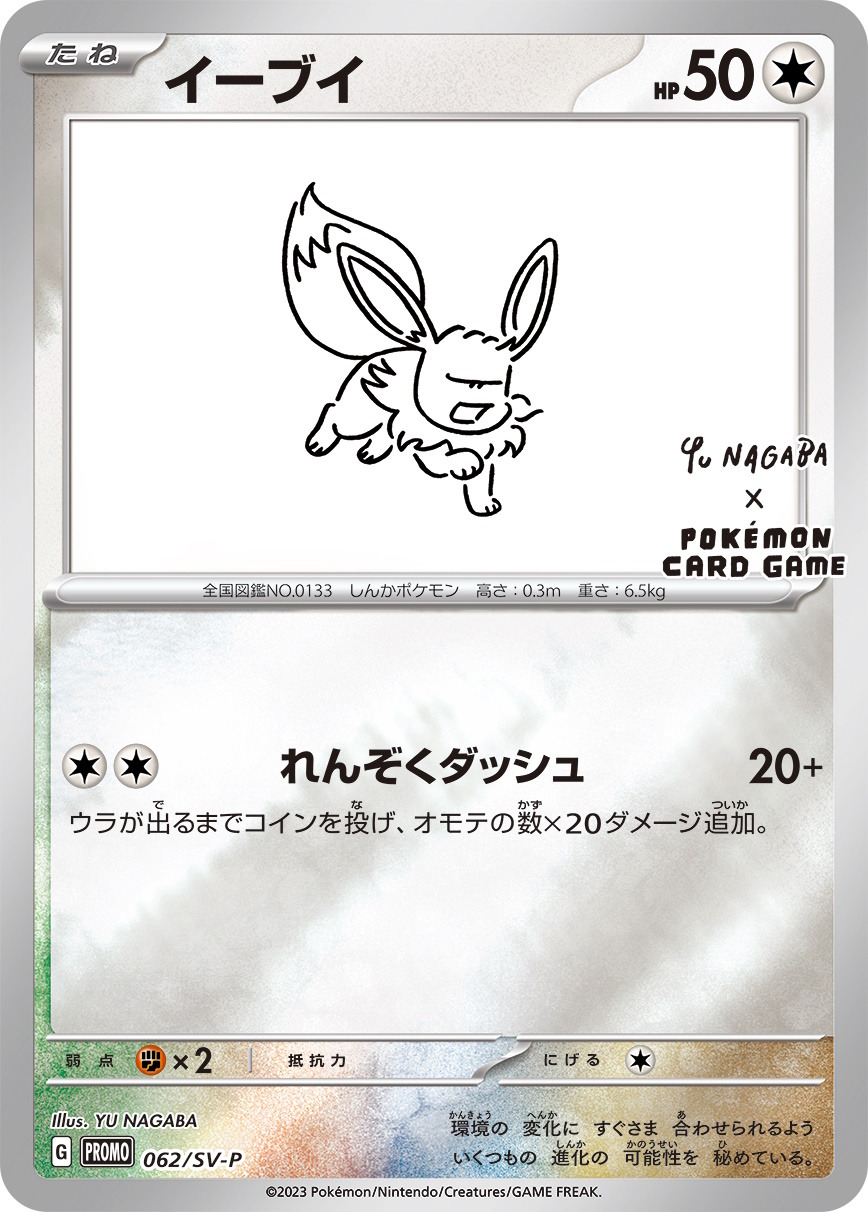
ポケカ』特別な「イーブイ」プロモカードが配布開始!人気アーティスト

2022人気の ポケモンカード 長場雄 YU NAGABA イーブイプロモ 10パック
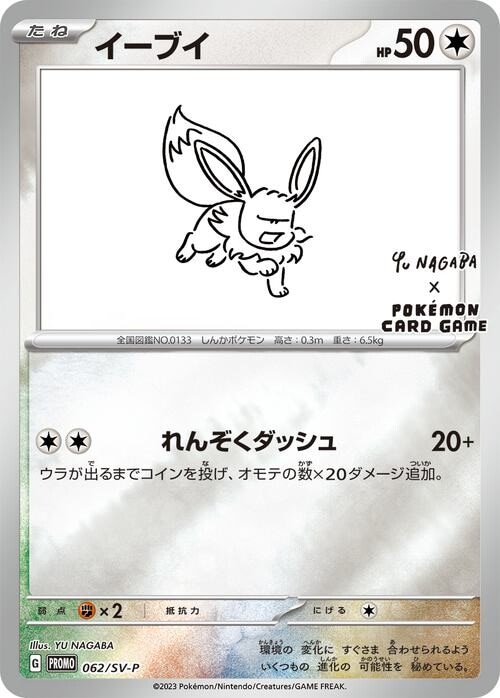
ポケモン プロモカード イーブイ 長場雄 - ポケモンカードゲーム

日本製】 プロモカードパック nagaba yu コンプリートセット コンプ 長

若者の大愛商品 ポケモンカード 長場雄 YU NAGABA イーブイ プロモ 30

クラシック ポケモンカード 長場雄 9種コンプセット プロモカード

30%OFF】 即日発送 ポケモンカード 長場雄 9種コンプセット プロモ

30%OFF】 YU NAGABA ポケモンカード イーブイズ プロモカード 長場雄

テレビで話題】 【ポケカ】YU NAGABA イーブイ 8枚セット プロモカード

購入し イーブイプロモ 長場雄 プロモカード YU NAGABA イーブイ

信頼 長場雄 プロモカード9種コンプセット ブイズ ポケモンカード
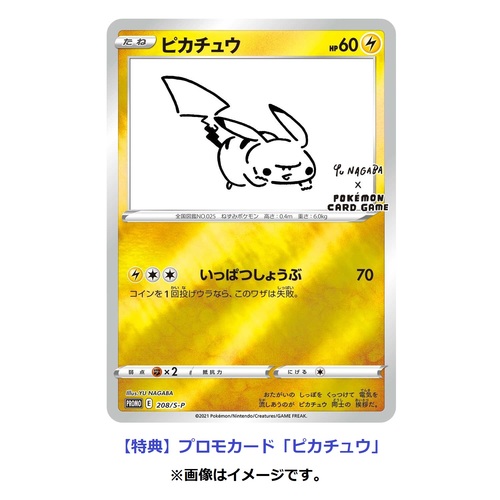
ピカチュウ YU NAGABA × ポケモンカード 長場雄 プロモカード 限定
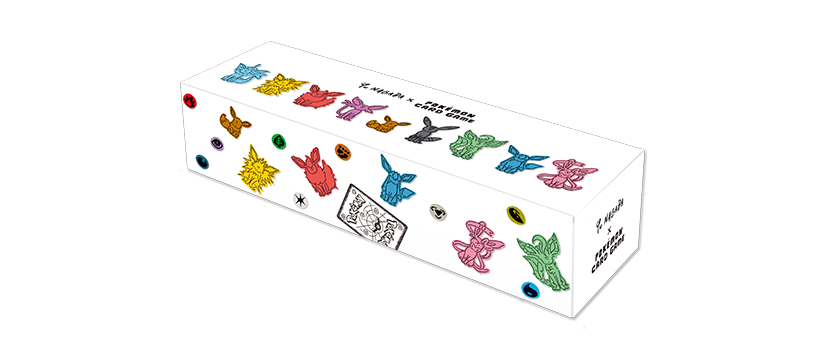
2023年5月24日(水)~】YU NAGABA × ポケモンカードゲーム | 転売クエスト

楽天スーパーセール】 長場雄 プロモカード ポケモンカード イーブイ

5年保証』 YU NAGABA×ポケモンカード イーブイ プロモカード 長場雄
ポケカ』特別な「イーブイ」プロモカードが配布開始!人気アーティスト

高評価の贈り物 未開封 ポケモンカード 長場雄 プロモカード ブイズ

ポケモンカード 長場雄 yu nagaba イーブイ プロモカード 安価 8869円

特別セール品】 ポケモンカード 長場雄 YU NAGABA イーブイプロモ 8

未開封 ポケモンカード 長場雄 YU NAGABA イーブイ プロモ 9パック

50%OFF】 ポケモンカード 長場雄 プロモ 20パック ポケモンカード

ポケモンカード 長場雄 YU NAGABA イーブイ プロモ 未開封10パック

大放出セール】 ピカチュウ 長場雄 プロモカード ポケモンカードゲーム

ポケモンカード YU NAGABA 長場雄 プロモ カード イーブイ 20パック

ポケモン×長場雄 ピカチュウ プロモカード nagaba

プロモカード、スペシャルBOX…[YU NAGABA ×ポケモンカードゲーム

値引きする ポケモンカード 長場雄 10パックセット 未開封 プロモ

ピカチュウ YU NAGABA × ポケモンカード 長場雄 プロモカード 限定

限定特価】 ポケモンカード 長場雄 ② プロモカードパック コラボ

ポケモンカード yu nagaba 長場雄 イーブイ プロモカード20パック

ポケモンカード 長場雄 YU NAGABA プロモカード ブイズ 8種 格安販売中

経典 ポケモンカード 長場雄 イーブイ プロモカード コンプリート 9枚

注目ショップ・ブランドのギフト 長場雄 ポケモンカード プロモカード

超新作】 ポケモンカード 長場雄 イーブイ プロモ 10パック ポケモン

限定セール!】 ポケモンカード 長場雄 YU NAGABA イーブイ プロモ 20p

最安値【新品未開封】プロモ 長場雄 ピカチュウ ポケモンカード


商品の情報
メルカリ安心への取り組み
お金は事務局に支払われ、評価後に振り込まれます
出品者
スピード発送
この出品者は平均24時間以内に発送しています














